How To Perform A Vulnerability assessment, full Step by step guide
What is a Vulnerability ?
In cybersecurity, a vulnerability is a weakness that can be exploited by cyber-criminals to gain unauthorized access to a computer system.
what is a vulnerability assessment ?
A vulnerability assessment is an analysis of vulnerability/bugs in IT system at a certain point in time with the aim of identifying the system's weakness before hackers can get hold of theme.
Difference Between vulnerability assessment & Penetration Testing
- Vulnerability:-
Vulnerability assessment is an automated test, meaning a tool does all of the work and generate the report at the end.
What is the purpose of a Vulnerability Assessment ?
A vulnerability assessment test some or all of your systems & generates a detailed vulnerability report.
this report can then be used to fix the problems uncovered to avoid security breaches.
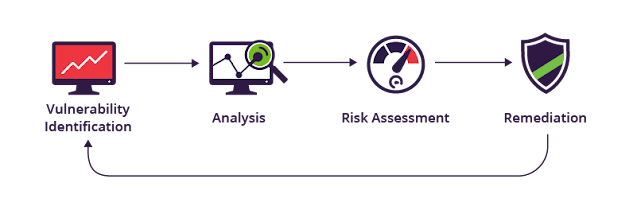
Step to conduct A vulnerability Assessment: -
- Asset Discovery
First, you need to decide what you want to scan, the discovery aspect of this process can be targely automated.
- Prioritization
Once you know what you've got, the next question is whether you can afford to run a vulnerability assessment on all of it.
Prioritization can help where budgets can't cover every asset the company owns.
- Vulnerability Scanning
vulnerability assessment are designed to identify known security weakness and provide guidance on how to fix them.